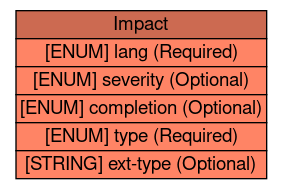
The Impact class allows for categorizing and describing the technical impact of the incident on the network of an organization.
digraph Impact {
graph [bb="0,0,204,134",
rankdir=LR
];
node [label="\N"];
Impact [height=1.8611,
label=<<table BORDER="0" CELLBORDER="1" CELLSPACING="0"> <tr> <td BGCOLOR="#cc6a51" HREF="/idmef_parser/IODEFv1/Impact.html" TITLE="The Impact class allows for categorizing and describing the technical impact of the incident on the network of an organization. "><FONT FACE="Nimbus Sans L">Impact</FONT></td> </tr>" %<tr><td BGCOLOR="#ff8465" HREF="/idmef_parser/IODEFv1/Impact.html" TITLE="A valid language code per RFC 4646 [7] constrained by the definition of "xs:language". The interpretation of this code is described in Section 6."><FONT FACE="Nimbus Sans L">[ENUM] lang (Required)</FONT></td></tr>%<tr><td BGCOLOR="#ff8465" HREF="/idmef_parser/IODEFv1/Impact.html" TITLE="An estimate of the relative severity of the activity. The permitted values are shown below. There is no default value."><FONT FACE="Nimbus Sans L">[ENUM] severity (Optional)</FONT></td></tr>%<tr><td BGCOLOR="#ff8465" HREF="/idmef_parser/IODEFv1/Impact.html" TITLE="An indication whether the described activity was successful. The permitted values are shown below. There is no default value."><FONT FACE="Nimbus Sans L">[ENUM] completion (Optional)</FONT></td></tr>%<tr><td BGCOLOR="#ff8465" HREF="/idmef_parser/IODEFv1/Impact.html" TITLE="Classifies the malicious activity into incident categories. The permitted values are shown below. The default value is "other"."><FONT FACE="Nimbus Sans L">[ENUM] type (Required)</FONT></td></tr>%<tr><td BGCOLOR="#ff8465" HREF="/idmef_parser/IODEFv1/Impact.html" TITLE="A means by which to extend the type attribute. See Section 5.1."><FONT FACE="Nimbus Sans L">[STRING] ext-type (Optional)</FONT></td></tr>%</table>>,
pos="102,67",
shape=plaintext,
width=2.8333];
}
