Method
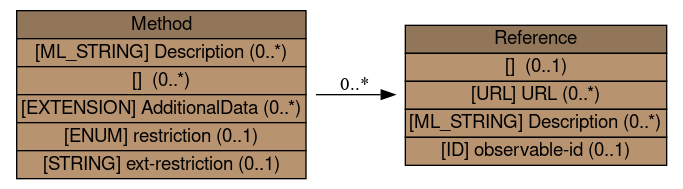
The Method class describes the tactics, techniques, procedures, or weakness used by the threat actor in an incident. This class consists of both a list of references describing the attack methods and weaknesses and a free-form text description.
digraph Method { graph [bb="0,0,504,134", rankdir=LR ]; node [label="\N"]; Method [height=1.8611, label=<<table BORDER="0" CELLBORDER="1" CELLSPACING="0"> <tr> <td BGCOLOR="#92765a" HREF="/idmef_parser/IODEFv2/Method.html" TITLE="The Method class describes the tactics, techniques, procedures, or weakness used by the threat actor in an incident. This class consists of both a list of references describing the attack methods and weaknesses and a free-form text description. "><FONT FACE="Nimbus Sans L">Method</FONT></td> </tr>" %<tr><td BGCOLOR="#b79370" HREF="/idmef_parser/IODEFv2/Method.html" TITLE="A free-form text description of techniques, tactics, or procedures used by the threat actor."><FONT FACE="Nimbus Sans L">[ML_STRING] Description (0..*)</FONT></td></tr>%<tr><td BGCOLOR="#b79370" HREF="/idmef_parser/IODEFv2/Method.html" TITLE="A reference to the exploited weakness per [RFC7203]."><FONT FACE="Nimbus Sans L">[] (0..*)</FONT></td></tr>%<tr><td BGCOLOR="#b79370" HREF="/idmef_parser/IODEFv2/Method.html" TITLE="A mechanism by which to extend the data model."><FONT FACE="Nimbus Sans L">[EXTENSION] AdditionalData (0..*)</FONT></td></tr>%<tr><td BGCOLOR="#b79370" HREF="/idmef_parser/IODEFv2/Method.html" TITLE="See Section 3.3.1."><FONT FACE="Nimbus Sans L">[ENUM] restriction (0..1)</FONT></td></tr>%<tr><td BGCOLOR="#b79370" HREF="/idmef_parser/IODEFv2/Method.html" TITLE="A means by which to extend the restriction attribute. See Section 5.1.1."><FONT FACE="Nimbus Sans L">[STRING] ext-restriction (0..1)</FONT></td></tr>%</table>>, pos="116.5,67", shape=plaintext, width=3.2361]; Reference [height=1.5694, label=<<table BORDER="0" CELLBORDER="1" CELLSPACING="0"> <tr> <td BGCOLOR="#92765a" HREF="/idmef_parser/IODEFv2/Reference.html" TITLE="The Reference class is an external reference to relevant information such as a vulnerability, IDS alert, malware sample, advisory, or attack technique. "><FONT FACE="Nimbus Sans L">Reference</FONT></td> </tr>" %<tr><td BGCOLOR="#b79370" HREF="/idmef_parser/IODEFv2/Reference.html" TITLE="Reference identifier per [RFC7495]."><FONT FACE="Nimbus Sans L">[] (0..1)</FONT></td></tr>%<tr><td BGCOLOR="#b79370" HREF="/idmef_parser/IODEFv2/Reference.html" TITLE="A URL to a reference."><FONT FACE="Nimbus Sans L">[URL] URL (0..*)</FONT></td></tr>%<tr><td BGCOLOR="#b79370" HREF="/idmef_parser/IODEFv2/Reference.html" TITLE="A free-form text description of this reference."><FONT FACE="Nimbus Sans L">[ML_STRING] Description (0..*)</FONT></td></tr>%<tr><td BGCOLOR="#b79370" HREF="/idmef_parser/IODEFv2/Reference.html" TITLE="See Section 3.3.2."><FONT FACE="Nimbus Sans L">[ID] observable-id (0..1)</FONT></td></tr>%</table>>, pos="398,67", shape=plaintext, width=2.9444]; Method -> Reference [label="0..*", lp="262.5,74.5", pos="e,291.92,67 233.03,67 249.03,67 265.47,67 281.48,67"]; }
Aggregates
Reference (0..*)
A reference to a vulnerability, malware sample, advisory, or analysis of an attack technique. See Section 3.11.1.
Description (0..*)
A free-form text description of techniques, tactics, or procedures used by the threat actor.
(0..*)
A reference to the exploited weakness per [RFC7203].
AdditionalData (0..*)
A mechanism by which to extend the data model.
restriction (0..1)
See Section 3.3.1.
ext-restriction (0..1)
A means by which to extend the restriction attribute. See Section 5.1.1.